Network
Discovery Windows
DNS
1.
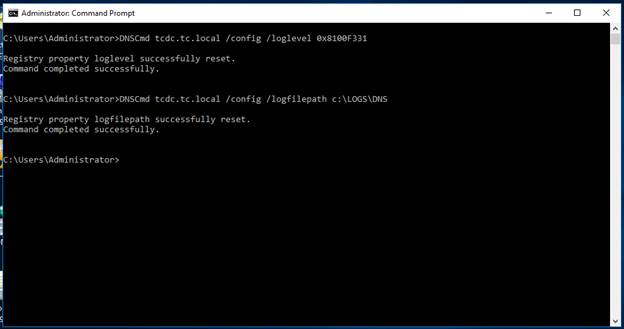
Open a command prompt as admin and run
the following commands:
DNSCmd <FQDN_Server_name>
/config /logLevel 0x8100F331
(Enables complete DNS logging)
DNSCmd < FQDN_Server_name
> /config /LogFilePath c:\LOGS\DNS
(Sets the path for the log file)
2.
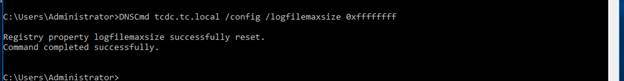
Next run:
DNSCmd < FQDN_Server_name
> /config /logfilemaxsize 0xffffffff
(Set the log file max size to about 4GB in size)
3.
Navigate to the logging path and open
the log file:
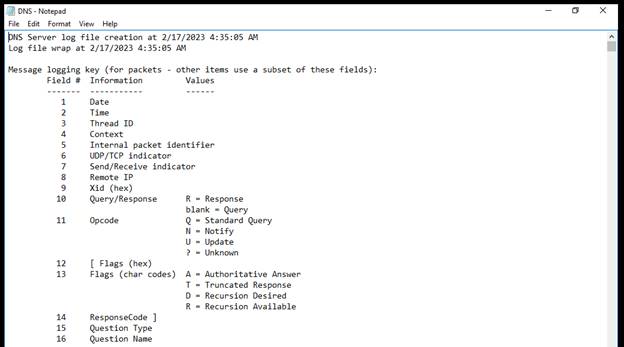
Here ^ we see the key to let us know what we are looking at in the log.
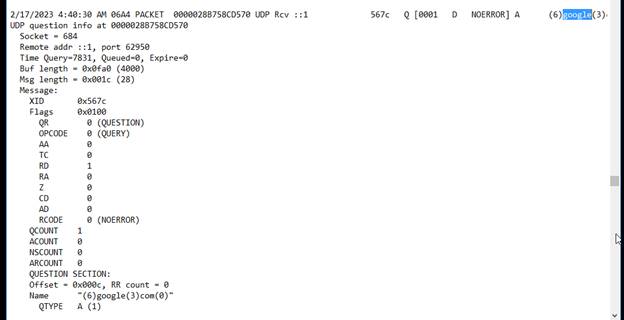
Here ^ we see the DNS query information for google.com.
Why Monitor DNS?
Monitoring DNS logs is essential for maintaining the
security of your network, detecting, and responding to potential threats,
ensuring optimal network performance, and quickly resolving any connectivity
issues. It provides insights into the communication patterns of devices within
your network and helps you make informed decisions to enhance your overall
network infrastructure.
1.
Security
Malware Detection: DNS logs can reveal patterns of malicious activity such as
communication with known malicious domains or botnet command and control
servers. Monitoring DNS queries can help detect malware infections within your
network.
Data Exfiltration Detection: Attackers might use DNS for data exfiltration by
encoding sensitive information into DNS queries or responses. Monitoring these
logs can help detect such suspicious activities.
2.
Threat Intelligence
Identifying Threats: By analyzing DNS logs, you can identify domains associated
with phishing, ransomware, or other cyber threats. This information can be used
to strengthen your security measures and block access to malicious sites.
3.
Anomaly Detection
Unusual Behavior: Monitoring DNS logs allows you to spot abnormal patterns of
DNS activity. For example, a sudden surge in DNS requests might indicate a
malware outbreak or a potential Distributed Denial of Service (DDoS) attack.
4.
Compliance and Auditing
Record Keeping: DNS logs provide a record of domain name queries and responses,
which can be crucial for compliance requirements or auditing purposes.
5.
Policy Enforcement
Content Filtering: DNS logs can be used to enforce content filtering policies
by monitoring which domains users are attempting to access. This is
particularly important in organizations where strict internet usage policies
are in place.