Network
Discovery Windows
Enable DHCP server logging on Server 2016+ with
PowerShell below.
1.
Open PowerShell and input the following
syntax:
Set-DhcpServerAuditLog -ComputerName
<FQDN of server> -Enable $True -Path "C:\Logs\DHCP\" -MaxMBFileSize 100
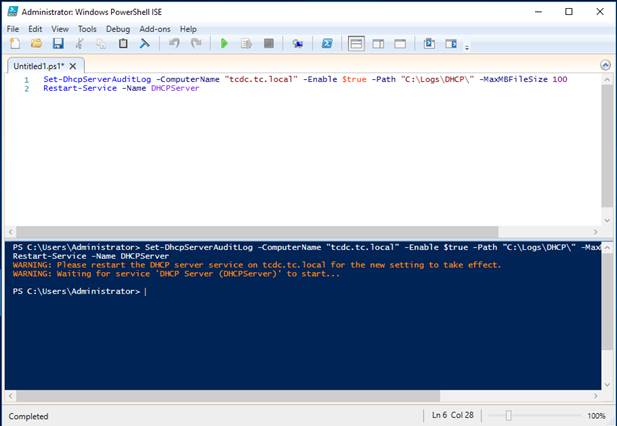
( It will prompt you to restart the DHCP server service in the above example
the command is followed by:
Restart-Service -Name DHCPServer)
2.
Navigate to the log path we specified in
step 1 to view the events:
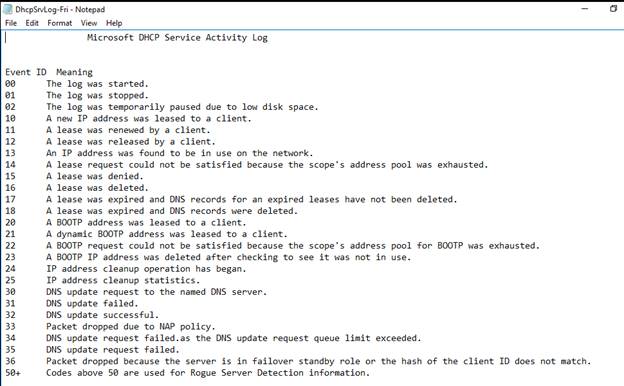
Here ^ we see the Event ID codes to know what number correlates with what type
of event.
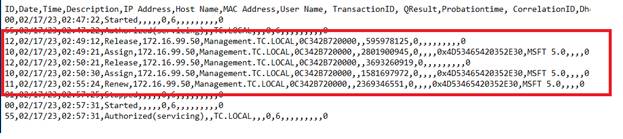
Here ^ we see the new IP Address lease activity for machine Management when
the ipconfig -release and ipconfig -renew commands were executed.
Why Monitor DHCP?
Monitoring DHCP logs provides a proactive approach
to network management, security, and troubleshooting. It helps you maintain a
secure and efficient network environment while enabling faster responses to
potential issues or threats.
1.
Network Security
DHCP logs can help detect unauthorized devices or potential security breaches.
Monitoring these logs can help you identify rogue devices that have managed to
connect to your network without proper authorization. Unrecognized devices
could be a sign of unauthorized access or even a potential cyberattack.
2.
Identify Malicious Activity
Anomalous patterns in DHCP logs, such as frequent IP address changes, rapid
address lease times, or suspicious hostnames, can indicate malicious activity
such as an attempt to evade detection, distribute malware, or launch attacks
like distributed denial-of-service (DDoS).
3.
Compliance and Auditing
For organizations subject to industry regulations or security standards,
monitoring DHCP logs can aid in compliance and auditing efforts. It provides a
record of network activity and can be useful for demonstrating compliance with
security policies.
4.
Incident Response
In the event of a security incident or breach, DHCP logs can serve as evidence
and provide a timeline of events. This information is invaluable for
post-incident analysis and remediation.