Scanning and Vulnerabilities
Nessus
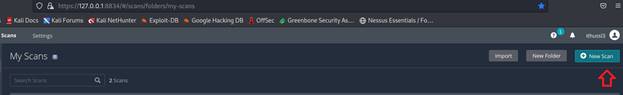
1. Login
to the Nessus Server and select New Scan at the top right-hand side:
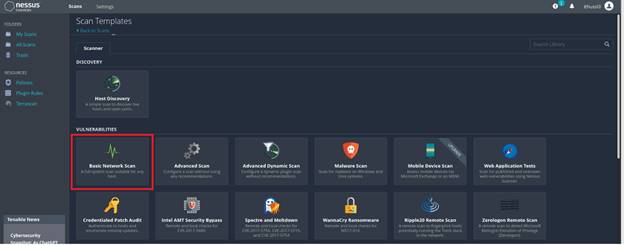
2. Choose
Basic Network Scan from the menu under Vulnerabilities:
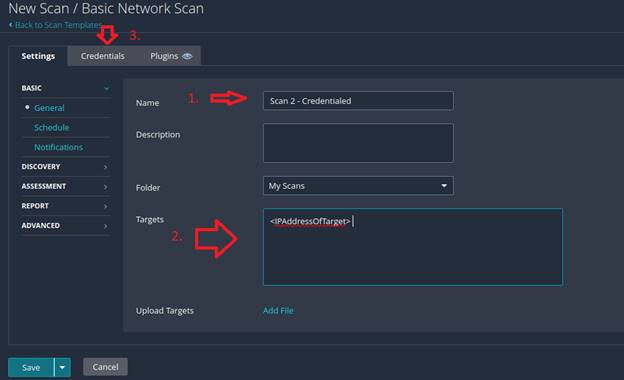
3. Give
your scan a Name and input your target(s) by typing them in or uploading a text
file with multiple targets reachable on the network, then Click Credentials:
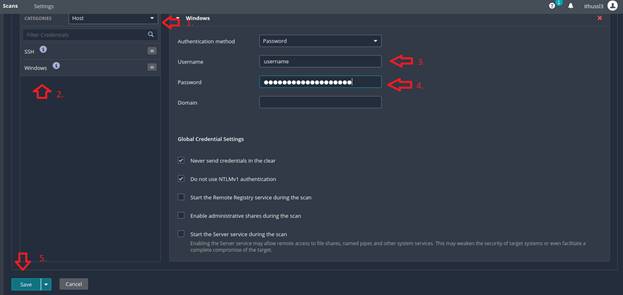
4. Under
Categories you can choose the type of target for the scan. In this example we
will use Host. As we are scanning a Windows 10 host click Windows in the left-hand
pane then input the username and password with an account with the required
access to perform the scan, then click Save.
5. Click
the Start button towards the right to being the scan:
6. This
will take some time. In a real scenario this would be performed after hours or
during a maintenance window and can take several hours pending the scope of the
assessment.
Once the scan is complete click it to see the findings:
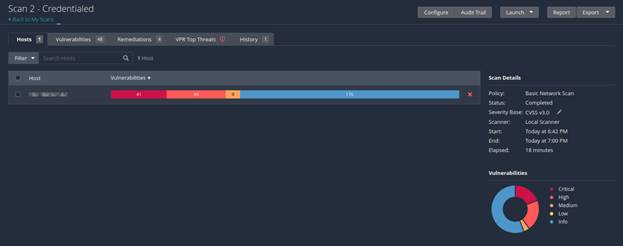
7. The
Vulnerabilities tab will list each finding with an associated CVSS score.
The Remediations tab will guide you on what remediation actions should be taken
to fix the identified vulnerability.
The VPR Top Threats page will provide suggested priority of remediation based
on the findings.
The History tab will show the history of the scan. How many times it ran and
when.
8. Resources
for setting up and troubleshooting credentialed scans:
https://docs.tenable.com/nessus/Content/CredentialedChecksOnWindows.htm
https://support.eventsmanager.gfi.com/hc/en-us/articles/360015155480-Opening-Ports-in-the-Windows-Firewall-Using-GPO
https://gfisoftware.my.salesforce-sites.com/support/articles/Skynet_Article/how-to-enable-remote-registry-through-group-policy
https://community.tenable.com/s/article/Troubleshooting-Credential-scanning-on-Windows