NMAP
A port is a logical endpoint for communication in an operating system. It's
used to distinguish specific services or processes that are running on a
computer. Ports are identified by numbers, ranging from 0 to 65535. For
example, web traffic is usually sent over port 80 for HTTP and port 443 for
HTTPS. Ports allow different applications and services to run concurrently on a
single computer without interfering with each other's communication.
1. Ping
sweep network for online nodes:
nmap -sn -PE 172.16.99.0/24
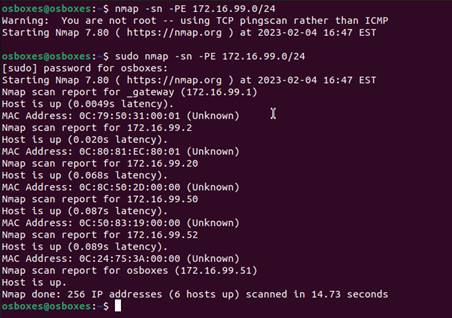
Here we see that there are 6 hosts up, identifying their IP and MAC addresses.
2. Scan
for open ports:
nmap open 172.16.99.0/24
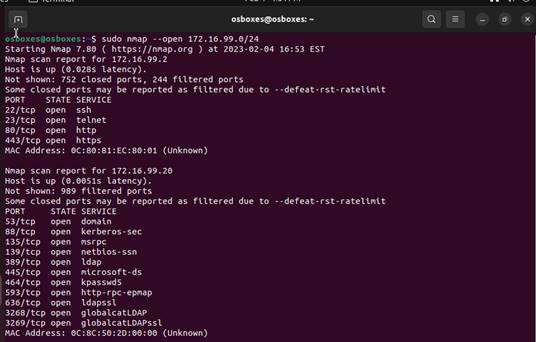
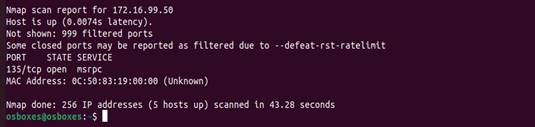
Notice that the port state only shows open as this is what was specified. So,
we know that these ports are actively listening and available. This is where we
would review these ports and evaluate if they are necessary to have in use.
3. Scan
for open services:
nmap -sV 172.16.99.0/24
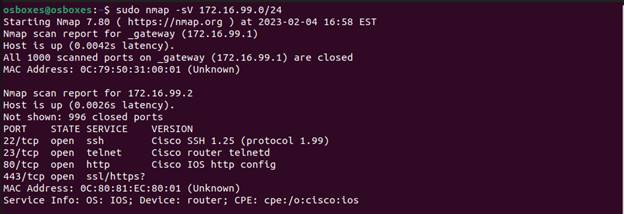
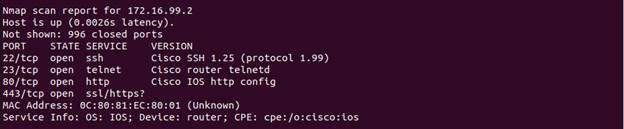
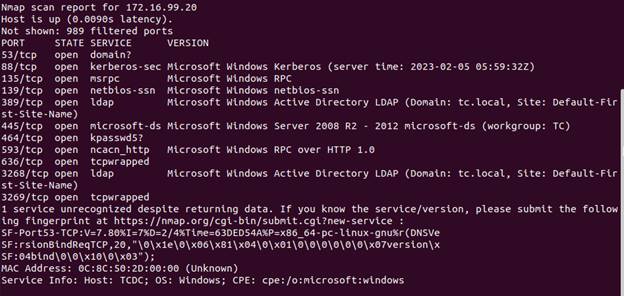
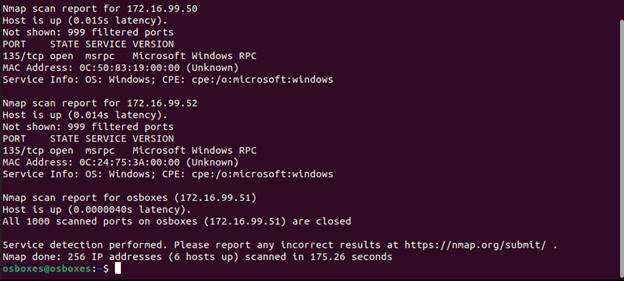
Here we see various services that are open on the hosts in this network. Again,
we would evaluate if these need to be open. Out the gate we know that telnet on
.2 should be shut down.
4. Scan
common TCP ports HTTP and HTTPS:
nmap -p 80,443 172.16.99.0/24
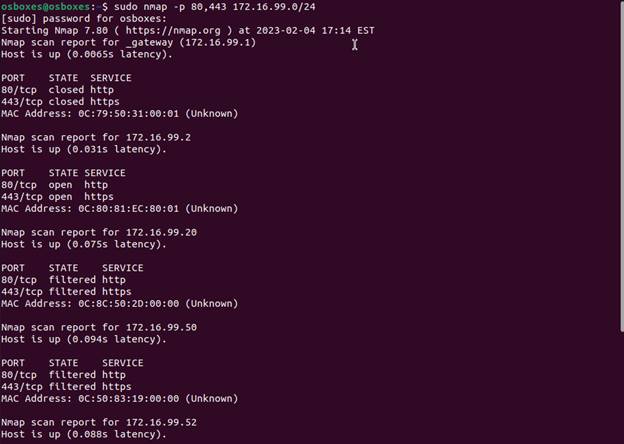
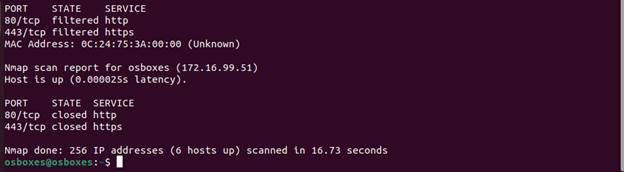
Here we see that HTTP/HTTPS are open on .2, closed on .51, and filtered on the
rest. Using curl can test these services to see if nmaps findings are
accurate.
5. Scan
common UDP port DNS:
nmap -sU -p 53 172.16.99.0/24
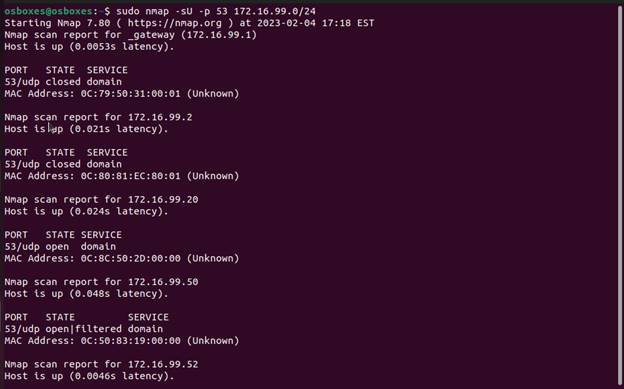
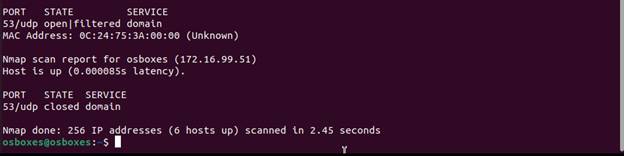
Here we see the state of the DNS port 53.
6. Scan
UDP and TCP on single host verbosely with optional skip ping:
nmap -v -Pn -sU -sT -p U:53,111,137,T:21-25,80,139,8080 172.16.99.20
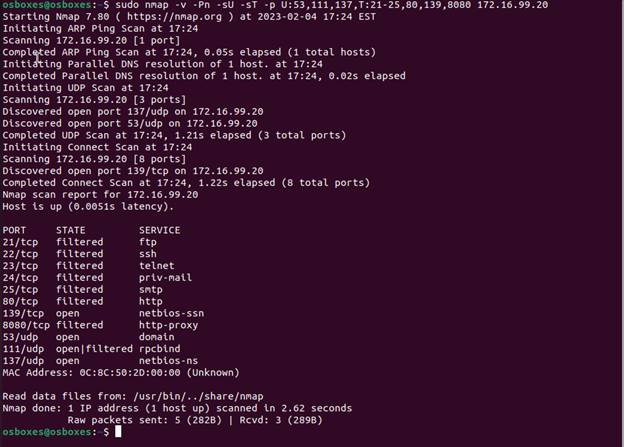
Here we see an output for both TCP and UDP ports for the host in question. Once
again, we would evaluate if these ports should be opened to minimize attack
surface.